
On Tuesday, Google made client-side encryption available to a limited group of Gmail and Calendar users in a move designed to give them more control over who sees sensitive communications and schedules.
Client-side encryption is a general term for any type of encryption that is applied to data before it is sent from a user’s device to a server. By contrast, with server-side encryption, a client device sends data to a central server, which then uses the keys in its possession to encrypt it while it is stored. This is what Google is doing today. (To be clear, the data is sent encrypted through HTTPS, but is decrypted once Google receives it.)
Google’s client-side encryption occupies a middle ground between the two. The data is encrypted on the client device before it is sent (via HTTPS) to Google. Data can only be decrypted on the endpoint device with the same key used by the sender. This provides an additional benefit because the data will remain unreadable to either Google Insiders or malicious hackers who manage to compromise Google’s servers.
In CSE short, client-side encryption was already available for Google Drive, Docs, Slides, Sheets, and Meet users of Google Workspace, which the company sells to businesses. Starting Tuesday, Google will roll it out to Gmail and Calendar Workspace customers.
“Workspace already encrypts data at rest and in transit using secure cryptographic libraries by design,” Ganesh Chillakapati, Google Group Product Manager for Google Workspace, and Andy Wynne, Product Management Manager for Google Workspace Security, books. “Client-side encryption with this encryption capability takes this encryption capability to the next level by ensuring that customers have sole control over their encryption keys — and thus full control over all access to their data.”
It would probably be an exaggeration to say that Google CSE gives customers “sole control” over their encryption keys. This is because CSE keys can be managed by a few third-party encryption key services that partner with Google. Technically, this means that these providers will have at least some control over the switches. Google gives CSE users the option to set up their main service with a Google API.
CSE is very different from the PGP (Privacy Good) mail encryption that was popular with security-conscious people a decade ago. This system provided true end-to-end encryption where the contents could only be decrypted with a key in the recipient’s possession. The difficulty of managing a different key for each end eventually proved too cumbersome, especially on a large scale, so the use of PGP has largely disappeared and has been replaced by end-to-end encryption implementations such as Signal.
Here is an overview of the workspace data CSE does not protect and does not protect:
| service | Data encrypted on the client side | data that no encrypted on the client side |
|---|---|---|
| Google Drive |
|
|
| gmail |
|
|
| google calendar |
|
Any content other than the event description, attachments, and Meet data, such as:
|
| Google is dead |
|
|
The aim of the CSE is to occupy organizations that have stringent compliance requirements that are imposed by law or contractual obligations. CSE gives these customers more control over the data Google stores while at the same time making it easier for authorized users to decrypt to share and collaborate.
“Users can continue to collaborate across other core apps in Google Workspace while IT and security teams can ensure sensitive data remains in compliance with regulations,” Google’s post on Tuesday said. “Because customers retain control of the encryption keys and the identity management service accesses those keys, sensitive data is not decryptable to Google and other outside entities.”
Google published last year this video Designed to show what the user experience is.
Solve digital sovereignty with Google Workspace.
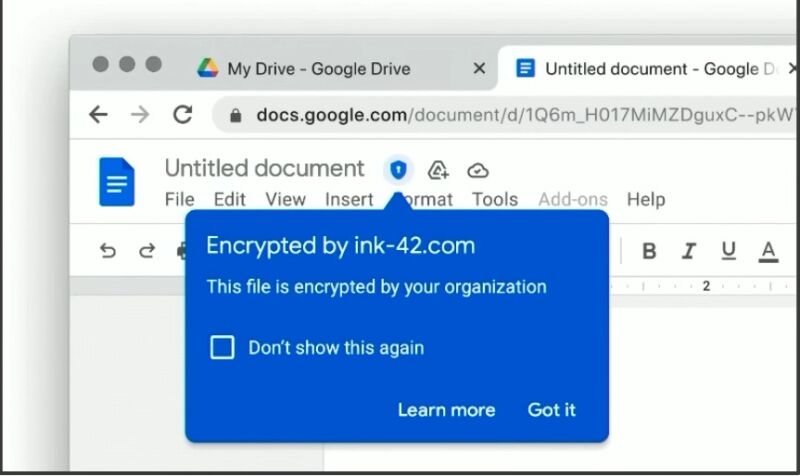
The blue circle with the shield in the following images indicates that content in documents, calendars, or video chats is protected by CSE:
Of course, CSE only works if the software hasn’t been changed. Should it be maliciously altered to store keys or copy unencrypted data, all bets are off.
Overall, Custom Search Engine provides an incremental improvement over the current protections available from Google. People and organizations with specific uses or requirements may find them useful, but they are unlikely to be demanded by the masses anytime soon.

“Certified food guru. Internet maven. Bacon junkie. Tv enthusiast. Avid writer. Gamer. Beeraholic.”






More Stories
Google hints at ‘amazing things’ coming in Android 17 as AI takes center stage
Nintendo is launching a music app with themes from Mario and Zelda, and more importantly, a Wii Shop channel
The Google Pixel Tablet 3 will take another step towards replacing your laptop